Authentication and AD Settings
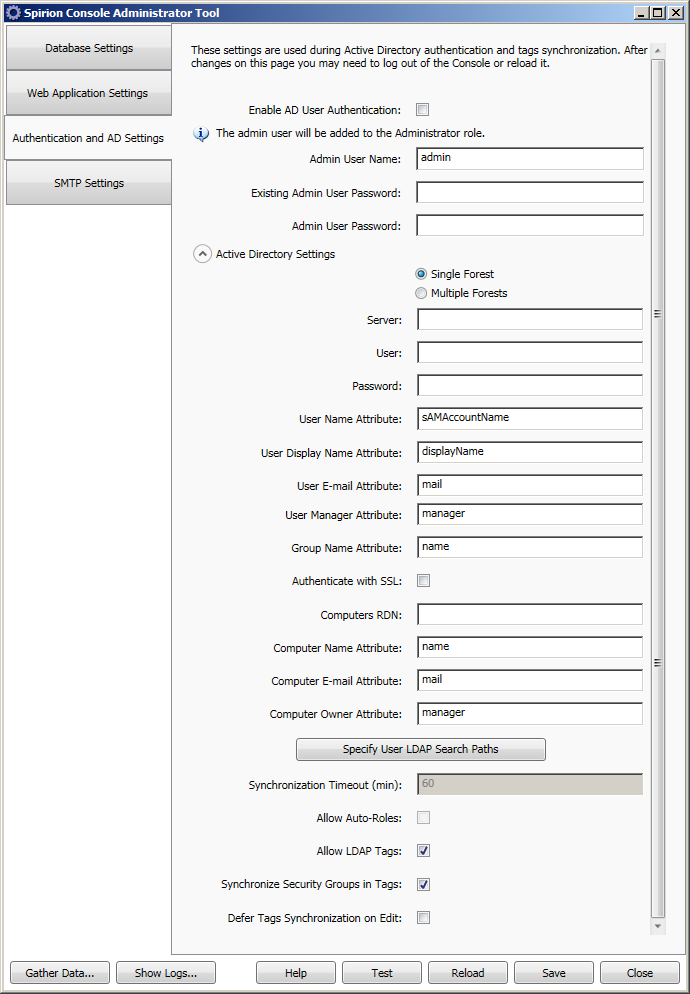
The Authentication and AD Settings tab displays settings for configuring Active Directory for usage in AD Authentication and for usage in LDAP tag synchronization. The descriptions below guides you in completing the appropriate connection information; however, in most cases a qualified Windows administrator with in-depth LDAP connection string knowledge should be consulted. After filling out connection information the Test button should be used to determine if the connection information is correct for the specific environment being accessed.
 How do I launch the Console Administrator Tool (CAT)?
How do I launch the Console Administrator Tool (CAT)?
| Field | Description |
|---|---|
| Enable AD User Authentication | If checked, the Console uses Active Directory to authenticate users. In order for Active Directory authentication to work a valid AD user must be identified in the Admin User Name field. When you enable AD User Authentication, you are prompted to create the Synchronize AD Users Service Job. When a user account is deleted from the Console by the Synchronize AD Users service job, any tags, reports or service jobs that were owned by the user that created them are also deleted. To preserve those tags, reports and service jobs please ensure you specify a fallback owner to assign them to. For detailed information, please refer to Synchronize AD Users service job. |
| Admin User Name | If Enable AD User Authentication is checked, this needs to be set to an existing user in Active Directory. This user is granted the Administrator role in the Console. If Enable AD User Authentication is not checked, this is set to the default of 'admin.' |
| Existing Admin User Password | In order to change the admin user password, you must provide an existing password. This field is not active if Enable AD Authentication is checked. |
| Admin User Password | This is the password for the admin user. This is only used when the admin account is locked out and automatically reset. This field is not active if Enable AD User Authentication is checked. |
| Account Locked - Click to Unlock | After five failed attempts trying to log in to the Console using the default admin account due to an incorrect password being entered, the account is locked out. To unlock the default admin account, click the Account locked – click to unlock button. When the unlock action completes a dialog displays to inform you that the admin account has been unlocked. You are then able to log in to the Console. This button only displays if the default admin user account has been locked out. This button displays when the admin account is locked. |
| Single Forest | Single Forest is the default configuration. |
| Multiple Forests | Multiple Forests, if enabled, allows you to work in active directories across multiple servers which allows you to synchronize AD users, tags, tasks, and roles. When Multiple Forests is enabled, then the Admin account that is specified should either be done in the format ldap://server.idf.local:389/CN=John Smith,CN=Users,DC=idf,DC=local or the username attribute can be set to userPrincipalName and the account name can take the format jsmith@idf.local. |
| Server |
The LDAP path to the Active Directory or LDAP server in the format of LDAP://Hostname[ :PortNumber ][ /DistinguishedName ]. The brackets ( [ ] ) indicate optional parameters. LDAPS is not configured with this parameter. More information about the LDAP ADsPath format can be found at http://msdn.microsoft.com/en-us/library/aa746384(VS.85).aspx All LDAP configurations are different and connection strings are case sensitive. In some cases you need to use an upper case LDAP:// connection string and in others you need to use a lower case ldap:// string. It is recommended that both are tried if things are not working properly. In general LDAP:// should always work, especially when sAMAccountName is used as the User Name Attribute. When the userPrincipalName is the User Name Attribute, then the lower case ldap:// might be required. Please consult a qualified windows administrator with in depth LDAP connection string knowledge to troubleshoot any connection issues. If you wish to use Secure LDAP (LDAPS) Do not use LDAPS://. |
| User | The username to bind with to the LDAP server. The user name varies greatly and various methods are known to work such as "username@your.domain", "YOURDOMAIN\user", and "user." |
| Password | The authentication password to use to connect to the LDAP server. The password is limited to 127 characters. |
| User Name Attribute | The LDAP attribute name used to identify the user name of a user. By default this is userPrincipalName, however in some configurations that may be sAMAccountName. As with most LDAP related properties these entries are case sensitive. Please consult a qualified windows administrator with in depth LDAP connection string knowledge to troubleshoot any connection issues. |
| User Display Name Attribute | When this value is set for a user in AD, the Display Name for the corresponding user in the Console is populated from that field when the Synchronize AD Users service job executes. |
| User Email Attribute | The LDAP attribute name used to identity the email address of a user. |
| User Manager Attribute | The LDAP attribute name used to identify a user indicated as a manager of an owner of an endpoint. The users' managers are synchronized during the execution of the Synchronize AD Users service job. The default value for this field is 'manager'. To set a user as a manager for an endpoint owner, you need to set the 'manager' attribute in your AD for a user and that user needs to be an Endpoint Owner in the Console. The value you set the manager to can be a path or a GUID as a string or bytes. (For example, if you wanted to designate the user 'admin' as a manager for the user "JHammond", you would edit the AD for "JHammond" to look like this: "Attribute: manager; Value: CN=admin,CN=Users,DC=domain,DC=com"). The value you enter in the User Manager Attribute field in the CAT should be the name of the attribute set in AD which in our example is 'manager'. Next you would enter "JHammond" as an Endpoint owner or let it auto populate when the Synchronize AD Users service job is run and the manager is set in the Console db on the JHammond user (all related AD users are synchronized in the Console’s db). |
| Group Name Attribute | The LDAP attribute name used to identify the group name of a group in the Active Directory Domain. The default attribute is “name” and is used during the synchronization of AD groups and users membership in groups during the Synchronize AD Users service job. As with most LDAP related properties these entries are case sensitive. Please consult a qualified windows administrator with in depth LDAP connection string knowledge to troubleshoot any connection issues. |
| Authenticate with SSL | If enabled, LDAP-SSL is used when authenticating to the server. |
| Computers RDN | The relative Distinguished Name (DN) for searching the computers in. This is an optional parameter and it can be empty. |
| Computer Name Attribute | The attribute of the computer object to use as the endpoint name. |
| Computer Email Attribute | When this value is set, the value stored in that attribute in AD for the endpoint populates the Email field of the Edit Endpoint dialog. These updates occur when the Synchronize Tags service job executes. |
| Computer Owner Attribute | When this value is set, the related value stored in that attribute in AD for the endpoint populates the Owners field of the Edit Endpoint dialog. These updates occur when the Synchronize Tags service job executes. |
| Specify User LDAP Search Paths | This allows you to add specific OU paths to search for user accounts to log in to the Console. The OUs listed here, if any, are the only ones searched when populating the Users page. If no OU paths are selected, then the entire AD structure is searched for user accounts. The format for LDAP Search Paths is the AD based simple path relative to the root of the AD but not including the root information such as the domain, for example "OU=UserGroup1". If there is a more complex path, such as a subgroup, just list the simple path in bottom up order, for example if the AD directory tree displays UserGroup4\UserGroup4_Subgroup1, the path would be "OU=UserGroup4_Subgroup1,OU=UserGroup4". LDAP paths are immediately verified and prompts appears if the OUs cannot be found. To enter paths click on the Specify User LDAP Search Paths button, and then when the Manage User LDAP Search Paths dialog appears type in a search path and click the Add button: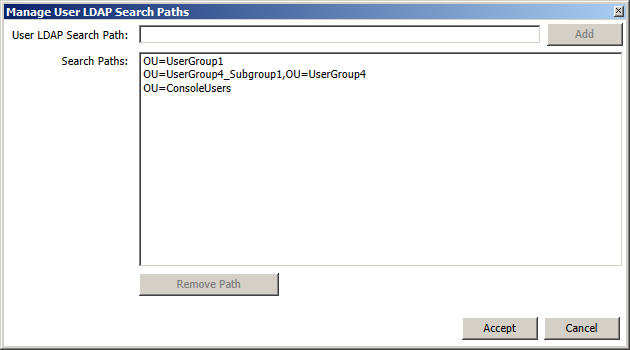 |
| Synchronization Timeout (min) | |
| Allow Auto-Roles | Enable AD User Authentication must be checked before you can enable this option. If enabled, Allow Auto-Roles synchronizes users with roles. |
| Allow LDAP Tags | If enabled, allows tags to be created from LDAP queries in the Console. |
| Synchronize Security Groups in Tags | When this option is enabled, the LDAP tags include AD security groups. The option is enabled by default. |
| Defer on Edit (affects Filter tags) |
If enabled, editing of an Active Directory tag does not immediately repopulate it. In this case the endpoints within the tag are updated during the Synchronize Tags service job. This may affect the any filter tags you have created. Note: When a user account is deleted from the Console by the Synchronize AD Users service job, any tags, reports or service jobs that were owned by that user is also deleted. If you want to preserve those tags, reports and service jobs you must select a new owner to assign them to. For more detailed information, refer to the Synchronize AD Users Service Job for article. |
The common buttons at the bottom of the CAT can be used as follows on the Authentication and AD Settings page:
| Field | Description |
|---|---|
| Help | Use this button to open a browser window with context sensitive help. |
| Save | Use this button to save configuration changes made to the Authentication and AD Settings. This button should be pressed once all desired changes are complete and before the Test button is used. After the Save button is pressed, a confirmation dialog displays that reads, "The settings were saved successfully." |
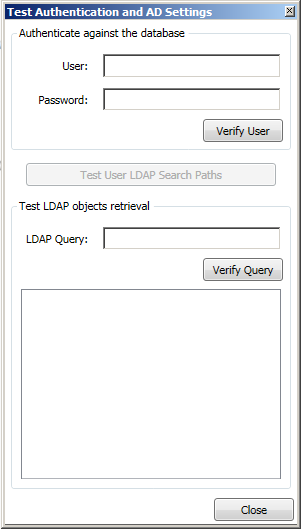
| Test |
Use this button to test the authentication settings. A test dialog displays requiring further configuration information. Once the additional configuration information is provided click the Verify User button to test a user account or the Verify Query button to test an Active Directory LDAP query. Any errors are displayed if the user or query verifications fail. The test dialog requires the following information:
|
| Reload | Use this button to reload the IIS configuration with the updated authentication settings. |
| Close | Use this button to close the CAT. Before clicking the Close button, make sure that you have saved any desired changes by clicking the Save button or the changes are lost. |